Sci-fi becomes reality as University of Washington lab uses strands of DNA to hack into a computer, but experts say there’s no cause for concern
Researchers from the University of Washington say they have successfully hacked into a computer using custom strands of DNA for the first time.
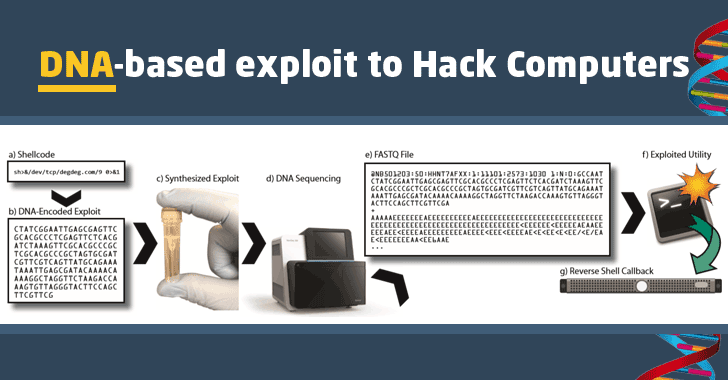
Akin to something from the pages of science fiction, the researchers used the life-encoding molecule to attack and take over a computer, using strands of DNA to transmit a computer virus from the biological to the digital realm.
“We designed and created a synthetic DNA strand that contained malicious computer code encoded in the bases of the DNA strand,” wrote the researchers led by Tadayoshi Kohno and Luis Ceze from the Paul G Allen school of computer science and engineering at the University of Washington.
“When this physical strand was sequenced and processed by the vulnerable program it gave remote control of the computer doing the processing. That is, we were able to remotely exploit and gain full control over a computer using adversarial synthetic DNA.”
The researchers used the four bases in DNA, adenine, cytosine, guanine and thymine – A, C, G and T – to encode their malware, which when read by a piece of DNA sequencing equipment converted the molecular code into computer code capable of taking over the computer connected to the DNA sequencer.
The hack was only possible because of weakness in the DNA sequencing software, and only in this specific instance. The researchers say that there is no reason for concern: “Note that there is not present cause for alarm about present-day threats. We have no evidence to believe that the security of DNA sequencing or DNA data in general is currently under attack.”
Instead the researchers are using their results to illustrate the need for better security within the DNA sequencing systems in use today. The idea for the research came from an analysis of the commonly used open-source sequencing software, which processes and analyses the results from sequencing machines, found cybersecurity weaknesses and a failure to follow security best practices meaning that they could be vulnerable to attack.
The results show that it is technically possible to use DNA as a way to transfer malware and attack vulnerabilities in the sequencing compute program.
“It is time to improve the state of DNA security,” say the researchers. “We again stress that there is no cause for people to be alarmed today, but we also encourage the DNA sequencing community to proactively address computer security risks before any adversaries manifest.”
Research has already shown that it is possible to transfer data using DNA. In April 2016, Microsoft and the University of Washington demonstrated a technique for storing and retrieving digital images using DNA. That research aims to turn DNA into a viable storage medium for digital information, using its unique properties to store vast amounts of information in tiny amounts of liquid.
In July this year, scientists from Harvard managed to store moving pictures in the DNA of a living cell as part of researched aimed at creating a molecular data recorder that could sit inside living cells.
Since you’re here …
… we have a small favour to ask. More people are reading the Guardian than ever but advertising revenues across the media are falling fast. And unlike many news organisations, we haven’t put up a paywall – we want to keep our journalism as open as we can. So you can see why we need to ask for your help. The Guardian’s independent, investigative journalism takes a lot of time, money and hard work to produce. But we do it because we believe our perspective matters – because it might well be your perspective, too.
If everyone who reads our reporting, who likes it, helps to support it, our future would be much more secure.
Source: theguardian.com